Table of Contents
ToggleWhy Networking is Essential for Ethical Hacking
If you’re stepping into the world of ethical hacking, mastering networking isn’t just beneficial—it’s essential. The internet and private networks form the battleground where cyber threats emerge, and understanding how data moves, how devices interact, and where vulnerabilities lie is critical. Without a strong grasp of networking fundamentals, hacking is like trying to crack a safe without knowing how the lock mechanism works.
The Eye-Opening Reality of Cybersecurity
One of the biggest revelations I had when diving into cybersecurity was realizing that hacking is fundamentally about understanding networks. Every attack, every vulnerability, and every defense mechanism revolves around how data traverses a network. Whether it’s intercepting traffic, bypassing security measures, or exploiting system weaknesses, a hacker’s ability to manipulate networks is what makes the difference.
Key Networking Concepts Every Ethical Hacker Should Know
To excel in ethical hacking, you need a solid foundation in:
Device Communication – Understanding routers, switches, and IP addressing.
Data Flow – Learning the OSI and TCP/IP models, as well as key protocols like TCP, UDP, and HTTP.
Security Weaknesses – Identifying open ports, misconfigured firewalls, and weak encryption techniques.
Networking isn’t just about configuring Wi-Fi or connecting devices—it forms the backbone of every digital interaction. In cybersecurity, networking knowledge plays a crucial role in:
Reconnaissance & Footprinting – Identifying potential vulnerabilities within a network.
Exploitation – Gaining access through misconfigurations and security flaws.
Defense Strategies – Strengthening network security to mitigate cyber threats.
By developing a deep understanding of networking, you’re not just learning how systems communicate—you’re equipping yourself with the skills to secure them against ever-evolving cyber threats. Whether your goal is ethical hacking, penetration testing, or cybersecurity defense, networking is the foundation upon which all your skills will be built.
Now that we know why networking is critical for hacking, let’s dive into the foundational concepts that make it all work! 🚀

Foundational Networking Concepts
But before we get down to the details of hacking and penetration testing, let’s go a little backwards and set up the groundwork. Understanding how networks work will be like going through the rule book of some game before starting to play it. This section covers the key concepts that are an essential building block for an ethical hacker….
The OSI Model: Layers and Their Roles in Communication
Each layer plays a specific role in how data is sent, received, and processed on a network. Understanding these layers is crucial for hacking because you’ll need to know which layer to target when exploiting a vulnerability
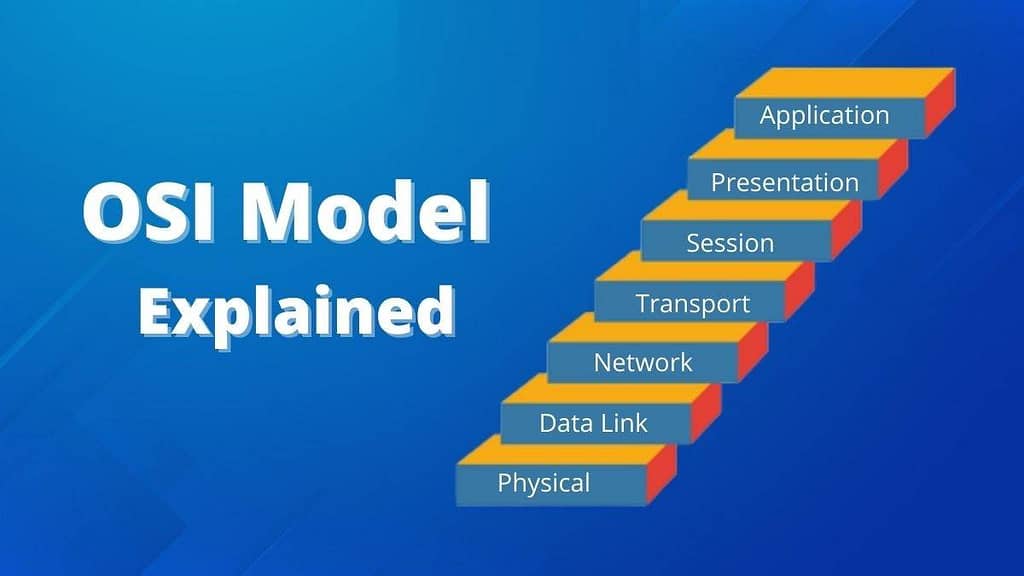
The OSI (Open Systems Interconnection) model breaks down how data travels across a network into 7 layers. It’s a helpful way to understand where different network activities happen. Here’s a quick overview of the layers:
- Physical Layer – This is the hardware layer. Think cables, switches, and physical connections.
- Data Link Layer – Deals with data transfer between devices on the same network (think MAC addresses).
- Network Layer – Handles routing and IP addressing (this is where we get our IP addresses).
- Transport Layer – Manages end-to-end communication between devices (e.g., TCP/UDP protocols).
- Session Layer – Manages sessions or connections between applications.
- Presentation Layer – Converts data into a format that can be understood by the application layer (like encryption/decryption).
- Application Layer – This is where users interact with applications like web browsers, email, etc.
TCP/IP Model: Simplifying Network Interactions
The TCP/IP model is a simpler, more practical approach to networking, and it’s the foundation of the Internet. It has only four layers:
- Network Access Layer—This layer combines the OSI’s physical and data link layers. It’s all about how data is physically transmitted on the network.
- Internet Layer – Corresponds to the OSI’s network layer and deals with IP addresses and routing
- Transport Layer – Equivalent to the OSI’s transport layer, handling end-to-end communication, typically using TCP or UDP.
- Application Layer – Covers everything from the OSI’s session, presentation, and application layers, supporting protocols like HTTP, FTP, DNS, etc.
IP Addressing: IPv4 vs. IPv6, Subnetting, and CIDR Notation
- IPv4 – The older, more common version, which uses 32-bit addresses (e.g., 192.168.1.1). This gives us around 4 billion possible addresses.
- IPv6 – The newer version, is designed to address IPv4’s limitations. It uses 128-bit addresses, allowing for an almost infinite number of devices (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334).

MAC Addresses: Hardware Identification and ARP
A MAC (Media Access Control) address is a unique identifier assigned to the network interface card(NIC) of a device. It’s like the device’s permanent fingerprint. Unlike IP addresses, MAC addresses operate at the Data Link Layer (Layer 2) and don’t change, making them important for identifying devices within the same network.
The ARP (Address Resolution Protocol) is used to map an IP address to a MAC address. This is how devices know the physical address of a device when they want to send data to it on a local network.
Understanding Different Types of Networks: LAN, WAN, MAN, GAN, and PAN
In today’s digital era, networking plays a crucial role in connecting devices and facilitating communication across various scales. Networks are classified based on their size, coverage, and purpose. This article explores five major types of networks: Local Area Network (LAN), Wide Area Network (WAN), Metropolitan Area Network (MAN), Global Area Network (GAN), and Personal Area Network (PAN).
1. Local Area Network (LAN)
A LAN connects computers and devices within a limited geographic area, such as a home, office, or campus. It enables high-speed data transfer and resource sharing, including printers and storage devices. Typically, LANs use Ethernet cables or Wi-Fi for connectivity, ensuring fast and secure communication within a small radius.
2. Wide Area Network (WAN)
WANs cover vast geographical areas, often spanning cities, countries, or even continents. Unlike LANs, which rely on internal networking infrastructure, WANs utilize leased telecommunication lines, satellite links, or fiber-optic cables. The internet itself is the largest example of a WAN, connecting billions of devices worldwide.
3. Metropolitan Area Network (MAN)
A MAN bridges the gap between LAN and WAN by covering a larger area than a LAN but remaining confined to a single metropolitan region, such as a city. MANs are often used by businesses, universities, and government agencies to establish a unified communication network across multiple locations within a city.
4. Global Area Network (GAN)
A GAN extends connectivity beyond national and continental boundaries, supporting international communication networks. It integrates multiple WANs and relies on satellite communications and global telecommunication infrastructure. Airlines, multinational corporations, and global research organizations frequently utilize GANs for seamless communication.
5. Personal Area Network (PAN)
A PAN is the smallest type of network, designed for personal device connectivity within a limited range. Common examples include Bluetooth connections between a smartphone and a smartwatch or a USB connection between a laptop and a printer. PANs facilitate short-range, direct communication for personal and professional use.
Network Topologies

Bus topology connects all devices to a single central cable, known as the bus or backbone. Data travels along this cable, and each device listens for its intended messages.
Advantages:
Cost-effective and easy to implement
Requires minimal cable compared to other topologies
Disadvantages:
Prone to data collisions
If the main cable fails, the entire network goes down

In a star topology, all devices are connected to a central hub or switch, which manages communication between them.
Advantages:
Easy to manage and troubleshoot
Network failure of a single device does not affect others
Disadvantages:
The central hub is a single point of failure
Requires more cable than bus topology

A ring topology forms a closed-loop where data flows in one direction (unidirectional) or both directions (bidirectional), reducing collision risks. Each device (node) is connected to exactly two other nodes, forming a continuous pathway for signals.
How Ring Topology Works:
Data travels in a circular manner from one node to another until it reaches its intended destination.
The data passes through each device in the network before reaching the target node.
In a unidirectional ring, data moves in only one direction, whereas in a bidirectional ring, data can travel in both directions, improving fault tolerance.
Types of Ring Topology:
Simple Ring Topology: Data moves in a single direction, and if one node fails, the entire network is affected.
Dual Ring Topology: Uses two rings (primary and secondary), where the secondary ring acts as a backup in case of a failure in the primary ring.
Advantages:
Reduces the chances of data collisions as data flows in an organized manner.
Performs well under heavy network traffic since each node has equal access to the network.
A dual-ring setup increases redundancy and fault tolerance.
Disadvantages:
A failure in a single node or cable in a simple ring topology can bring down the entire network.
Adding or removing nodes requires reconfiguration, leading to temporary network downtime.
Troubleshooting issues can be challenging due to the interconnected nature of the topology.

Tree topology combines multiple star networks into a hierarchical structure, where smaller networks branch from a main backbone.
Advantages:
Scalable for large networks
Allows better organization of devices
Disadvantages:
Dependent on the main backbone—failure can affect the entire network
Complex configuration and maintenance

Mesh topology provides multiple interconnections between nodes, ensuring redundancy and high reliability.
Types:
Full Mesh: Every node is directly connected to all others.
Partial Mesh: Some nodes have multiple connections, but not all.
Advantages:
High fault tolerance
Efficient data transfer with multiple communication paths
Disadvantages:
Expensive and complex to set up
Requires significant cabling and configuration
Core Network Protocols
Core network protocols are the fundamental communication rules that enable devices to exchange data across networks. These protocols define how data is formatted, transmitted, and received. Below are some of the essential network protocols:
1. Transmission Control Protocol/Internet Protocol (TCP/IP)
TCP/IP is the foundation of internet and network communication. It defines how data is packetized, addressed, transmitted, routed, and received across networks.
TCP (Transmission Control Protocol): Ensures reliable, ordered, and error-checked delivery of data.
IP (Internet Protocol): Handles addressing and routing of packets to ensure they reach the correct destination.
2. Hypertext Transfer Protocol (HTTP) & HTTPS
HTTP (Hypertext Transfer Protocol): Facilitates communication between web browsers and web servers.
HTTPS (Hypertext Transfer Protocol Secure): An encrypted version of HTTP using SSL/TLS for secure data transfer.
3. File Transfer Protocol (FTP) & Secure FTP (SFTP)
FTP: Used for transferring files between a client and a server.
SFTP (Secure File Transfer Protocol): Adds a layer of encryption using SSH for secure file transfers.
4. Domain Name System (DNS)
DNS translates human-readable domain names (e.g., www.example.com) into IP addresses that computers use to identify each other on the network.
5. Dynamic Host Configuration Protocol (DHCP)
DHCP automatically assigns IP addresses to devices on a network, reducing the need for manual configuration.
6. Simple Mail Transfer Protocol (SMTP) & Post Office Protocol (POP3) / Internet Message Access Protocol (IMAP)
SMTP: Used for sending emails.
POP3/IMAP: Used for retrieving and managing emails from mail servers.
7. Secure Shell (SSH)
SSH is a secure protocol that allows encrypted remote login and command execution over an unsecured network.
8. Internet Control Message Protocol (ICMP)
ICMP is used for network diagnostics and error reporting, commonly utilized by tools like ping and traceroute.
9. Address Resolution Protocol (ARP) & Reverse ARP (RARP)
ARP: Resolves IP addresses to MAC addresses.
RARP: Maps MAC addresses to IP addresses.
10. Simple Network Management Protocol (SNMP)
SNMP is used for monitoring and managing network devices like routers, switches, and servers.
